SNMPTT (SNMP Trap Translator) is an SNMP trap handler written in Perl for use with the Net-SNMP / UCD-SNMP snmptrapd program (www.net-snmp.org).
About
SNMPTT (SNMP Trap Translator) is an SNMP trap handler written in Perl for use with the Net-SNMP / UCD-SNMP snmptrapd program (www.net-snmp.org). SNMPTT supports Linux, Unix and Windows.
Many network devices including but not limited to network switches, routers, remote access servers, UPSs, printers and operating systems such as Unix and Windows NT have the ability to send notifications to an SNMP manager running on a network management station. The notifications can be either SNMP Traps, or SNMP Inform messages.
The notification can contain a wide array of information such as port failures, link failures, access violations, power outages, paper jams, hard drive failures etc. The MIB (Management Information Base) available from the vendor determines the notifications supported by each device.
The MIB file contains TRAP-TYPE (SMIv1) or NOTIFICATION-TYPE (SMIv2) definitions, which define the variables that are passed to the management station when a particular event occurs.
The Net-SNMP program snmptrapd is an application that receives and logs SNMP trap and inform messages via TCP/IP. Following is a sample syslog entry for a Compaq cpqDa3LogDrvStatusChange trap that notifies that the drive array is rebuilding:
Feb 12 13:37:10 server11 snmptrapd[25409]: 192.168.110.192: Enterprise Specific Trap (3008) Uptime: 306 days, 23:13:24.29, .1.3.6.1.2.1.1.5.0 = SERVER08, .1.3.6.1.4.1.232.11.2.11.1.0 = 0, .1.3.6.1.4.1.232.3.2.3.1.1.4.8.1 = rebuilding(7)
or
Feb 12 13:37:10 server11 snmptrapd[25409]: 192.168.110.192: Enterprise Specific Trap (3008) Uptime: 306 days, 23:13:24.29, sysName.0 = SERVER08, cpqHoTrapFlags.0 = 0, cpqDaLogDrvStatus.8.1 = rebuilding(7)
The output from snmptrapd can be changed via the -O option to display numeric or symbolic OIDs and other display options, but it generally follows the format of variable name = value, variable name = value etc.
A more descriptive / friendly trap message can be created using SNMPTT's variable substitution. Following is the same trap, logged with SNMPTT:
Feb 12 13:37:13 server11 TRAPD: .1.3.6.1.4.1.232.0.3008 Normal "XLOGONLY" server08 - Logical Drive Status Change: Status is now rebuilding
The definition for the cpqDa3LogDrvStatusChange trap in the SNMPTT configuration file would be defined as follows:
FORMAT Logical Drive Status Change: Status is now $3.
The $3 represents the third variable as defined in the MIB file, which for this particular trap, is the cpqDaLogDrvStatus variable.
Another example of an SNMPTT configuration entry is:
FORMAT Compaq Drive Array Spare Drive on controller $4, bus $5, bay $6 status is $3.
Which could result in the following output:
"Compaq Drive Array Spare Drive on controller 3, bus 0, bay 3 status is Failed."
Snmptt can log to any of the following destinations: text log, syslog, NT Event log or a SQL database. External programs can also be run to pass the translated trap to an email client, paging software etc.
In addition to variable substitution, SNMPTT allows complex configurations allowing:
- the ability to accept or reject a trap based on the host name, ip address, network range, or variable values inside of the trap enterprise variables
- execute external programs to send pages, emails etc
- perform regular expression search and replace on the translated message such as translating the variable value "Building alarm 4" to "Moisture detection alarm"
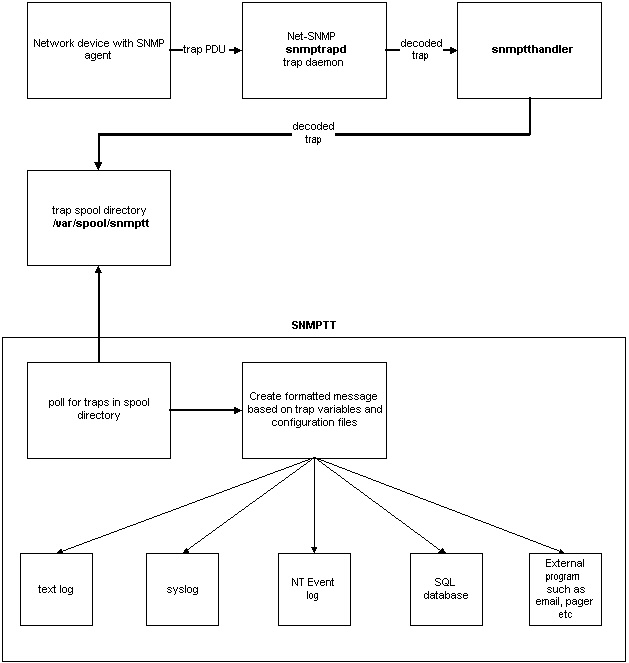
The following picture illustrates how the network device, Net-SNMP and SNMPTT are integrated to process a trap.
Downloads
All downloads are available from the SourceForge web site:
Prerequisete
In case of snmptt 1.2, you need the following packages and modules:
- Perl 5.6.1 and above
- Net-SNMP package
- net-snmp-5.1-2.1.i386.rpm
- net-snmp-utils-5.1-2.1.i386.rpm
- Perl modules
- Sys::Syslog
- Net-SNMP Perl
- Soket
- Time::HiRes
- Text::ParseWords
- Config::IniFiles
- Getop::Long
- Posix
To check the version of Perl, use perl -v. Use #rpm -qa | grep snmp to check whether your system already have Net-SNMP or not.
To check the installed Perl modules, use the following command:
#find `perl -e 'print join(" ", @INC)'` -type f -name "*.pm" > perl.txt
The installed packeges will be listed in perl.txt. If not installed, search and download from http://search.cpan.org/.
Install snmptt
#tar -zxvf snmptt_1.2.tgz
#cd snmptt_1.2
#cp -p snmptt /usr/sbin
#chmod 755 /usr/sbin/snmptt
#cp -p snmptt.ini /etc/snmp/
Install snmptrapd
#rpm -ivh net-snmp-5.0.9-2.90.1.i386.rpm
#rpm -ivh net-snmp-utils-5.0.9-2.90.1.i386.rpm
#rpm -qa | grep snmp
Configure snmptrapd
Open /etc/snmp/snmptrapd.conf with your text editor and add the following line to it:
traphandle default /usr/sbin/snmptt
In snmptrapd is installed by rpm, snmptrapd startup script is also available under /etc/init.d. Open this file to change the startup option (add -On option as follows):
OPTIONS="-On -s -u /var/run/snmptrapd.pid"
Start snmptrapd.
#/etc/init.d/snmptrapd start
Configure snmptt.ini
Change snmptt.ini to enable logging. With this change, any failure in trap processing will be logged.
#vi /etc/snmp/snmptt.ini
Change the values:
unknown_trap_log_enable = 1
unknown_trap_log_file = /var/log/snmpttunknown.log
Create snmptt.conf
Create snmptt.conf which is defined in the [TrapFiles] section in snmptt.ini. When the trap which is defined in snmptt.conf is received, it will be processed.
Sample file of snmptt.conf is included in the sample directory in the snmptt1.2.tgz. Copy it to /etc/snmp/ and edit it.
[TrapFiles]
# A list of snmptt.conf files (this is NOT the snmptrapd.conf file). The COMPLETE path
# and filename. Ex: '/etc/snmp/snmptt.conf'
snmptt_conf_files = < <END
/etc/snmp/snmptt.conf
END
snmptt.conf (definitions for device link down and link up)
Uncomment the lines as your needs.
EVENT linkDown .1.3.6.1.6.3.1.1.5.3 "Status Events" Normal
FORMAT Link down on interface $1. Admin state: $2. Operational state: $3
EXEC /usr/local/nagios/libexec/submit_check_result $r TRAP 2 "Link down on interface $1.
Admin state: $2. Operational state: $3"
SDESC
A linkDown trap signifies that the SNMP entity, acting in
an agent role, has detected that the ifOperStatus object for
one of its communication links is about to enter the down
state from some other state (but not from the notPresent
state). This other state is indicated by the included value
of ifOperStatus.
EDESC
#
#
#
EVENT linkUp .1.3.6.1.6.3.1.1.5.4 "Status Events" Normal
FORMAT Link up on interface $1. Admin state: $2. Operational state: $3
EXEC /usr/local/nagios/libexec/submit_check_result $r TRAP 0 "Link up on interface $1. Ad
min state: $2. Operational state: $3"
SDESC
A linkUp trap signifies that the SNMP entity, acting in an
agent role, has detected that the ifOperStatus object for
one of its communication links left the down state and
transitioned into some other state (but not into the
notPresent state). This other state is indicated by the
included value of ifOperStatus.
EDESC
With this configuration, snmptt defines the receiving event (OID) in EVENT section and runs the /usr/local/nagios/libexec/submit_check_result which is defined in EXEC section.
Create submit_check_result
snmpトラップを受けたときに実行されるシェルであるsubmit_check_resultを作成します
以下作成例です
[TrapFiles]#!/bin/sh
echocmd="/bin/echo"
CommandFile="/usr/local/nagios/var/rw/nagios.cmd"
datetime=`date +%s`
cmdline="[$datetime] PROCESS_SERVICE_CHECK_RESULT;$1;$2;$3;$4"
`$echocmd $cmdline >> $CommandFile`
snmptt.confで指定されたEXEC欄をみていただければわかりますが
EXEC /usr/local/nagios/libexec/submit_check_result $r TRAP 0 "Link up on interface $1. Admin state: $2. Operational state: $3"
$rはトラップを投げてきたホスト名が入ります。この$rがsubmit_check_resultの$1に入ります
同じようにsubmit_check_resultの$2にはTRAP、$3には"0"が入り
$4には"Link up on interface $1. Admin state: $2. Operational state: $3"が入ります
このトラップを受けてsubmit_check_resultシェルが動き、結果が/usr/local/nagios/var/rw/nagios.cmdに吐き出されていきます。nagiosはこの吐き出されたファイルの内容を見てアラートをあげるかどうかを判断します
SNMPトラップサービスをNagiosに設定する
ここまで設定が完了したらSNMPトラップをNagiosにサービスとして動作させられるように設定を
行います
localhost.cfgのservice項目に追加をします
以下設定例です
define service{
use local-service ; Name of service template to use
host_name sw01
service_description TRAP
active_checks_enabled 1
max_check_attempts 1
is_volatile 1
check_command check_dummy!0!"OK"
}
ファイルの状態(ログ)を見て状態の変更を行うのでis_volatileを1に設定します
また定期的にファイルの状態を確認するため再試行はおこないませんのでmax_check_attemptsも1に設定
します
設定の確認
設定の確認はsnmptt1.2.tgzを展開したときにできるexamplesディレクトリ下のsample-trap.generic
を使用します
sample-trap.genericの内容は以下のようになっていますので使用環境に合わせて編集
するといいでしょう
sw01
192.168.1.15
.1.3.6.1.2.1.1.3.0 31:18:27:02.00
.1.3.6.1.6.3.1.1.4.1.0 .1.3.6.1.6.3.1.1.5.3
.1.3.6.1.2.1.2.2.1.1.3 3
.1.3.6.1.2.1.2.2.1.7.3 2
.1.3.6.1.2.1.2.2.1.8.3 3
#/usr/sbin/snmptt < /usr/local/snmptt/snmptt_1.2/examples/sample-trap.generic
アラートがあがれば成功です。また実際使用するにはsnmpトラップをとばす設定を
各監視対象ホストに入れておく必要があります
Windowsであれば簡易SNMPプロトコロル、スイッチであればsnmp-server hostコマンドでトラップの
送り先(今回の場合NagiosのIPアドレス)を設定します


コメント